Service set (802.11 network)
In IEEE 802.11 wireless local area networking standards (including Wi-Fi), a service set (also known as extended service set or ESS) is a group of wireless network devices which are identified by the same SSID (service set identifier). SSIDs serve as "network names" and are typically natural language labels. A service set forms a logical network—that is operating with the same level 2 networking parameters—they are on the same logical network segment (e.g., IP subnet or VLAN).
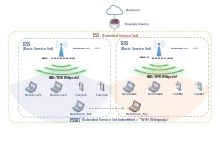
Basic service sets (BSS) are a subgroup of devices within a service set which are additionally also operating with the same physical layer medium access characteristics (i.e. radio frequency, modulation scheme, security settings etc.) such that they are wirelessly networked. Devices within basic service sets are identified by BSSIDs (basic service set identifiers), which are 48-bit labels that conform to MAC-48 conventions. While devices may have multiple BSSIDs, usually each BSSID is associated with at most one basic service set at a time.[1] There are two classes of basic service sets: those that are formed by an infrastructure mode redistribution point (access points or mesh nodes), and those that are formed by independent stations in a peer-to-peer ad hoc topology (an Independent Basic Service Set or IBSS.)
A basic service set should not to be confused with the coverage area of an access point, known as the 'basic service area' (BSA).[2]
Basic service sets (BSSs)
Infrastructure mode
An infrastructure mode wireless network basic service set (BSS) consists of one redistribution point — typically an access point (WAP or AP) — together with one or more "client" stations that are associated with (i.e. connected to) that redistribution point.[3] The operating parameters of the infrastructure-BSS are defined by the redistribution point. Stations communicate only with the redistribution point that they are associated with, and all traffic within the infrastructure-BSS is routed through/bridged by that redistribution point.
Each basic service set has its own unique identifier, a BSSID, which is a unique 48-bit identifier that follows MAC address conventions.[4] An infrastructure-BSSID is usually non-configurable, in which case it is either preset during manufacture, or mathematically derived from a preset value such as a serial number, the MAC address of the LAN connection, etc. As with the MAC addresses used for Ethernet devices, infrastructure-BSSIDs are a combination of a 24-bit Organization Unique Identifier (OUI, the manufacturer's identity) and a 24-bit serial number. A BSSID with a value of all 1s is used to indicate the wildcard BSSID, usable only during probe requests or for communications that take place outside the context of a BSS.[5]
Mesh basic service set
From the point of view of a wireless clients, IEEE 802.11s wireless mesh networks appear as a conventional infrastructure mode topology, and are centrally configured as such. The formation of the mesh's BSS, as well as wireless traffic management (including path selection and forwarding) is negotiated between the nodes (redistribution points) of the mesh infrastructure. The mesh's BSS is distinct from the networks (which may also be wireless) used by a mesh's redistribution points to communicate with one another.
Ad hoc
In contrast to the stations in an infrastructure-mode network, the stations in a wireless ad hoc network communicate directly with one another, i.e. without a dependence on a distribution point to relay traffic between them.[6] In this form of peer-to-peer wireless networking, the peers form an independent basic service set (IBSS).[7] Some of the responsibilities of a distribution point — such as defining network parameters and other "beaconing" functions — are established by the first station in an ad-hoc network. But that station does not relay traffic between the other stations; instead, the peers communicate directly with one another. Like infrastructure-BSSs, independent-BSSs also have a 48-bit MAC address-like identifier. But unlike infrastructure-BSS identifiers, independent-BSSs identifiers are not necessarily unique: the individual/group bit of the address is always set to 0 (individual), the universal/local bit of the address is always set to 1 (local), and the remaining 46 bits are randomly generated.[5]
Service set ID (WiFi)
The SSID is broadcast by stations in beacon packets to announce the presence of a network.
Unlike basic service set identifiers, SSIDs are usually customizable.[8] These SSIDs can be zero to 32 octets (32 bytes) long,[9] and are, for convenience, usually in a natural language, such as English. The 802.11 standards prior to the 2012 edition did not define any particular encoding/representation for SSIDs, which were expected to be treated and handled as an arbitrary sequence of 0–32 octets that are not limited to printable characters. The IEEE 802.11-2012 defines a tag that the SSID is UTF-8 encoded and when interpreting could contain any non-ISO basic Latin characters within it.[10] Wireless network stacks must still be prepared to handle arbitrary values in the SSID field.
Since the contents of an SSID field are arbitrary, the 802.11 standard permits devices to advertise the presence of a wireless network with beacon packets in which the SSID field is set to null.[11][n 1] A null SSID (the SSID element's 'length' field is set to zero[9]) is called a "wildcard SSID" in IEEE 802.11 standards documents,[12] and as a "no broadcast SSID" or "hidden SSID" in the context of beacon announcements,[11][13] and can be used, for example, in enterprise and mesh networks to steer a client to a particular (e.g. less utilized) access point.[11] A station may also likewise transmit packets in which the SSID field is set to null; this prompts an associated access point to send the station a list of supported SSIDs.[14] Once a device has associated with a basic service set, for efficiency, the SSID is not sent within packet headers; only BSSIDs are used for addressing.
Extended service sets (ESSs)
Formally, there is no distinct ESSID in the 802.11 standards.[15]cf. [16] In 802.11 standard documents, the logical network (ESS or independent-BSS) service set identifier is simply abbreviated SSID,[9] irrespective of whether an SSID identifies an infrastructure-BSS's ESS, or the peer-to-peer network of an independent-BSS.
An extended service set (ESS) is a set of one or more infrastructure basic service sets on a common logical network segment (i.e. same IP subnet and VLAN).[17] Key to the concept is that the participating basic service sets appear as a single network to the logical link control layer.[17][18] Thus, from the perspective of the logical link control layer, stations within an ESS may communicate with one another, and mobile stations may move transparently from one participating BSS to another (within the same ESS).[18] Extended service sets make possible distribution services such as centralized authentication and seamless roaming between infrastructure-BSSs. From the perspective of the link layer, all stations within an ESS are all on the same link, and transfer from one BSS to another is transparent to logical link control.[19]
The basic service sets formed in wireless ad hoc networks are, by definition, independent from other BSSs, and an independent-BSS cannot therefore be part of an extended infrastructure.[20] In that formal sense an independent-BSS has no extended service set. However, the network packets of both independent-BSSs and infrastructure-BSSs have a logical network service set identifier, and the logical link control does not distinguish between the use of that field to name an ESS network, and the use of that field to name a peer-to-peer ad hoc network. The two are effectively indistinguishable at the logical link control layer level.[19]
Notes
- To associate with a wireless network, a station must know the network's SSID. This information is either obtained from beacons broadcast by a base station (in which case a client can passively infer whether it is in range of that network), or — if no base station is advertising the SSID — a station must know the SSID beforehand by other means (e.g. from a previous configuration). When a client wishes to associate with a network, it sends the SSID in a probe request. An access point replies with a probe response if the SSID in a probe request is the wildcard SSID (SSID is zero-length) or matches a SSID that the access point supports[12] otherwise the access point does not respond to the probe request.
References
- "Understanding the Network Terms SSID, BSSID, and ESSID - Technical Documentation - Support - Juniper Networks". www.juniper.net.
- IEEE Std 802.11-2007, § 3.15, p. 5.
- IEEE Std 802.11-2007, § 3.16, p. 6.
- IEEE Std 802.11-2007, § 7.1.3.3, p. 6.
- IEEE Std 802.11-2007, § 7.1.3.3.3, p. 65.
- IEEE Std 802.11-2007, § 5.6, p. 41.
- IEEE Std 802.11-2007, § 5.21, p. 25.
- Vasseur & Dunkels 2010, p. 432.
- IEEE Std 802.11-2007, § 7.3.2.1, p. 101.
- IEEE (2012). "Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Sponsored by the LAN/MAN Standards Committee". IEEE 802.11-2012: 562.
- Murty, et al 2008, p. 75.
- IEEE Std 802.11-2007, § 11.1.3.2.1, p. 422.
- Dornseif, et al 2002, p. 2.
- Lindqvist, et al 2009, pp. 123f.
- Edney 2004, p. 11.
- IEEE Std 802.11-2007, Definitions, § 3, p. 8.
- IEEE Std 802.11-2007, § 3.54, p. 8.
- IEEE Std 802.11-2007, § 5.2.3.1, p. 26.
- Edney 2004, p. 8.
- IEEE Std 802.11-2007, § 5.6, p. 40.
Works cited
- Dornseif, Maximillian; Schumann, Kay H.; Klein, Christian (2002), "Tatsächliche und rechtliche Risiken drahtloser Computernetzwerke" (PDF), Datenschutz und Datensicherheit, 22 (4): 1–5.
- Edney, Jon (2004), "What is an ESS?", IEEE 802 LAN/MAN Standards Committee Meeting, July 2004, Piscataway, NJ: Institute of Electrical and Electronics Engineers.
- Lindqvist, Janne; Aura, Tuomas; Danezis, George; Koponen, Teemu; Myllyniemi, Annu; Mäki, Jussi; Roe, Michael (2009), "Privacy-preserving 802.11 Access-point Discovery", Proceedings of the Second ACM Conference on Wireless Network Security, WiSec '09, New York: ACM, pp. 123–130, CiteSeerX 10.1.1.206.4148, doi:10.1145/1514274.1514293, ISBN 978-1-60558-460-7, S2CID 8509913.
- Murty, Rohan; Padhye, Jitendra; Chandra, Ranveer; Wolman, Alec; Zill, Brian (2008), "Designing High Performance Enterprise Wi-Fi Networks" (PDF), in Crowcroft, Jon; Dahlin, Mike; et al. (eds.), Proceedings of the 5th USENIX Symposium on Networked Systems Design and Implementation, NSDI '08, Berkeley, CA: USENIX Association, pp. 73–88.
- Stacey, Robert; Ecclesine, Peter; et al., eds. (2010), "Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications, Amendment 6 (IEEE Std 802.11p-2010)" (PDF), Local and Metropolitan Area Networks, Specific Requirements, IEEE Standard for Information technology — Telecommunications and information exchange between systems, Piscataway, NJ: Institute of Electrical and Electronics Engineers, ISBN 978-0-7381-6324-6.
- Cole, Terry L.; Barber, Simon, eds. (2007), "Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications (IEEE Std 802.11-2007)" (PDF), Local and Metropolitan Area Networks, Specific Requirements, IEEE Standard for Information technology— Telecommunications and information exchange between systems., Piscataway, NJ: Institute of Electrical and Electronics Engineers, ISBN 978-0-7381-5656-9.
- Vasseur, Jean-Philippe; Dunkels, Adam (2010), Interconnecting Smart Objects with IP: The Next Internet, Burlington, MA: Morgan Kaufmann, ISBN 978-0-12-375166-9.