Physiological Signal Based Security
Body Area Networks (BANs) constantly interact with their physical environment with the help of sensors. Sensors collect process as well as communicate information gathered from their environment. Thus BANs are inherently cyber-physical systems. The BAN interacts with its physical world (human body) by collecting, processing, and communicating health data (vital signals, temperature, pressure) from the person. This information from the environment that is already being collected can be used to provide security to the BAN. Physiological Value based Security (PVS) uses the vital signals of the human body that is collected during health monitoring operation to provide usable security to BAN.[1]
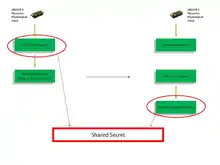
Properties of PVS
For PVS to succeed the scheme developed should have the following properties:
- The keys provided by PVS for security are long and random (a basic requirement in any security protocol).
- Knowing the physiological signals at any time will not provide significant advantage in knowing the keys agreed upon in future executions of the scheme, i.e. time variance (required to prevent attacker from guessing future feature values from present ones).
- The physiological stimuli used for PVS is universally (ensures that sensors at different location can measure the same signal).
- Knowing the physiological value of one individual will not provide significant advantage in guessing the keys being agreed by sensors on another individual, i.e. distinctiveness.
Implementation of PVS using Photoplethysmogram (PPG) signals
Plethysmogram based Key Agreement protocol (PKA) uses PPG signals to provide PVS infrastructure to the BAN. It provides secure key agreement between two sensors that wish to communicate in a BAN.
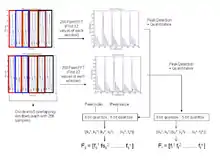
PKA has been divided into four basic steps as described in Figure 1:
- Sensing - PPG signals are sensed using Smith Medical pulse oximeter boards. The sampling rate of the instrument was 60 Hz. 12.8 seconds of PPG signals were sensed by the two communicating sensors.
- Generate features
- Frequency domain features were generated by performing 256 point overlapped windowed FFT on the measured signal. The signal was divided into five Hamming windows with an overlap of 50. The first 32 coefficients of the FFT of each of the windows are concatenated to form the frequency domain features. The FFT computation is shown in Figure 2.
- Peak Detection, Peaks (maxima) in the FFT coefficient curve were detected by detecting sudden change in slopes (from positive to negative) of the curve. Both the peak index and the peak values were noted.
- Quantization, The peak indexes were represented in 8 bits binary (since they could only take values from 1 to 160). The peak values were re-quantized into 16 non uniform levels. The first twelve levels were exponential while the next 4 levels were linear. The main reason for doing this was to extract the variations in the higher frequency components (with low coefficient values) in the FFT. Thus the peak values got quantized into 5 bits binary numbers.
- Secure Transmission of Features: Fuzzy Vault security primitive was used for secure transmission of the features from transmitting sensor to receiving sensor.
- Select Common Features.
References
- Cherukeri, Shriram; Venkatasubramanian, Krishna K.; Gupta, Sandeep K. S. (October 2003). Biosec: a biometric based approach for securing communication in wireless networks of biosensors implanted in the human body. Parallel Processing Workshops, 2003. Kaohsiung, Taiwan. doi:10.1109/MILCOM.2008.4753199.
- Venkatasubramanian, Krishna K.; Banerjee, Ayan; Gupta, Sandeep K. S. (November 2008). Plethysmogram-based Secure Inter-Sensor Communication in Body Area Networks. IEEE Military Communications Conference (MILCOM'08). San Diego, CA. doi:10.1109/MILCOM.2008.4753199.
- Venkatasubramanian, Krishna K.; Gupta, Sandeep K. S. (July 2010). "Physiological Value Based Efficient Usable Security Solutions for Body Sensor Networks". ACM Transactions on Sensor Network. 6 (4): 1–36. doi:10.1145/1777406.1777410.
- Venkatasubramanian, Krishna K.; Banerjee, Ayan; Gupta, Sandeep K. S. (January 2010). "PSKA: Usable and Secure Key Agreement Scheme for Body Area Networks". IEEE Transactions on Information Technology in Biomedicine. 14 (1): 60–8. doi:10.1109/TITB.2009.2037617. PMID 20007032.